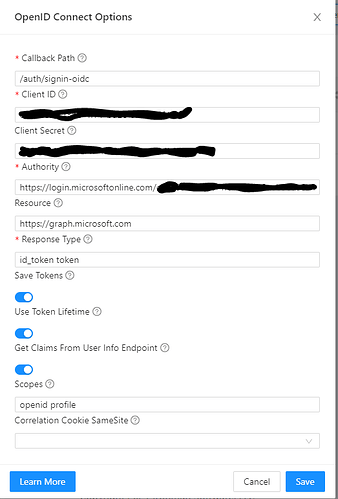
Just looping back around with this thread as I’m getting no where quick with OIDC.
I’ve been busy working on other projects and waiting on approval + changes for some networking for the last few months frustratingly, it’s taken a while but I’m finally back and ready to continue my journey with PSU in Azure.
I’ve just updated my web app to the latest 2.8.1 build.
Although still getting errors trying to enable OIDC - still not sure what I’m doing wrong here:

I’ve tried adding the OIDC config into my appsettings.json, then it shows in the Authentication page.
But after logging out of the admin account and trying to refresh, it just hangs and eventually throws a 500 error.
The OIDC settings I’ve basically replicated from an on-prem IIS version of PSU that I’d like to migrate to azure, only change I’ve made is I’ve added the new callback url to my app registration.
Here’s some snippets from my logs:
[17:32:46 INF] Azure Web Sites environment detected. Using 'C:\home\ASP.NET\DataProtection-Keys' as key repository; keys will not be encrypted at rest.
[17:32:51 ERR] Error registering vault PSUSecretStore
[17:32:51 ERR] Exception:
System.TypeInitializationException: The type initializer for 'Microsoft.PowerShell.SecretStore.SecureStoreFile' threw an exception.
---> System.UnauthorizedAccessException: Attempted to perform an unauthorized operation.
at System.Security.AccessControl.Win32.SetSecurityInfo(ResourceType type, String name, SafeHandle handle, SecurityInfos securityInformation, SecurityIdentifier owner, SecurityIdentifier group, GenericAcl sacl, GenericAcl dacl)
at System.Security.AccessControl.NativeObjectSecurity.Persist(String name, SafeHandle handle, AccessControlSections includeSections, Object exceptionContext)
at System.Security.AccessControl.NativeObjectSecurity.Persist(String name, AccessControlSections includeSections, Object exceptionContext)
at System.Security.AccessControl.NativeObjectSecurity.Persist(String name, AccessControlSections includeSections)
at System.Security.AccessControl.FileSystemSecurity.Persist(String fullPath)
at System.IO.FileSystemAclExtensions.SetAccessControl(DirectoryInfo directoryInfo, DirectorySecurity directorySecurity)
at Microsoft.PowerShell.SecretStore.SecureStoreFile.SetDirectoryACLs(String directoryPath)
at Microsoft.PowerShell.SecretStore.SecureStoreFile..cctor()
--- End of inner exception stack trace ---
at Microsoft.PowerShell.SecretStore.SecureStoreFile.get_ConfigRequiresPassword()
at Microsoft.PowerShell.SecretStore.LocalSecretStore.get_PasswordRequired()
at Microsoft.PowerShell.SecretStore.SetSecretStoreConfiguration.EndProcessing()
at System.Management.Automation.Cmdlet.DoEndProcessing()
at System.Management.Automation.CommandProcessorBase.Complete()
17:33:14 WRN] Error unprotecting the session cookie.
System.Security.Cryptography.CryptographicException: The key {9a7e39aa-8a9e-40b2-941e-9e6a36940eeb} was not found in the key ring.
at Microsoft.AspNetCore.DataProtection.KeyManagement.KeyRingBasedDataProtector.UnprotectCore(Byte[] protectedData, Boolean allowOperationsOnRevokedKeys, UnprotectStatus& status)
at Microsoft.AspNetCore.DataProtection.KeyManagement.KeyRingBasedDataProtector.DangerousUnprotect(Byte[] protectedData, Boolean ignoreRevocationErrors, Boolean& requiresMigration, Boolean& wasRevoked)
at Microsoft.AspNetCore.DataProtection.KeyManagement.KeyRingBasedDataProtector.Unprotect(Byte[] protectedData)
at Microsoft.AspNetCore.Session.CookieProtection.Unprotect(IDataProtector protector, String protectedText, ILogger logger)
^^^ This one repeats ALOT
[17:34:46 ERR] An unhandled exception has occurred while executing the request.
System.NullReferenceException: Object reference not set to an instance of an object.
at UniversalAutomation.Services.AuthenticationMethodsConfigurationScript.OnWriteBeforeAsync(AuthenticationMethod item) in D:\a\universal\universal\src\Universal.Server\Services\Configuration\AuthenticationMethods.cs:line 72
at UniversalAutomation.Services.ConfigurationScript`1.WriteAsync(T item, Identity identity) in D:\a\universal\universal\src\Universal.Server\Services\Configuration\ConfigurationScript.cs:line 95
at UniversalAutomation.Services.UniversalConfigurationService.WriteAsync(Object item, Identity identity) in D:\a\universal\universal\src\Universal.Server\Services\UniversalConfigurationService.cs:line 183
at UniversalAutomation.Services.UniversalConfigurationService.WriteAndSyncAsync[T](T item, Identity identity) in D:\a\universal\universal\src\Universal.Server\Services\UniversalConfigurationService.cs:line 162
at UniversalAutomation.SettingsController.NewAuthenticationMethod(AuthenticationMethod authenticationMethod) in D:\a\universal\universal\src\Universal.Server\Controllers\SettingsController.cs:line 157
at Microsoft.AspNetCore.Mvc.Infrastructure.ActionMethodExecutor.TaskOfIActionResultExecutor.Execute(IActionResultTypeMapper mapper, ObjectMethodExecutor executor, Object controller, Object[] arguments)
at Microsoft.AspNetCore.Mvc.Infrastructure.ControllerActionInvoker.<InvokeActionMethodAsync>g__Logged|12_1(ControllerActionInvoker invoker)
at Microsoft.AspNetCore.Mvc.Infrastructure.ControllerActionInvoker.<InvokeNextActionFilterAsync>g__Awaited|10_0(ControllerActionInvoker invoker, Task lastTask, State next, Scope scope, Object state, Boolean isCompleted)
at Microsoft.AspNetCore.Mvc.Infrastructure.ControllerActionInvoker.Rethrow(ActionExecutedContextSealed context)
at Microsoft.AspNetCore.Mvc.Infrastructure.ControllerActionInvoker.Next(State& next, Scope& scope, Object& state, Boolean& isCompleted)
at Microsoft.AspNetCore.Mvc.Infrastructure.ControllerActionInvoker.InvokeInnerFilterAsync()
--- End of stack trace from previous location ---
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.<InvokeNextResourceFilter>g__Awaited|24_0(ResourceInvoker invoker, Task lastTask, State next, Scope scope, Object state, Boolean isCompleted)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.Rethrow(ResourceExecutedContextSealed context)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.Next(State& next, Scope& scope, Object& state, Boolean& isCompleted)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.InvokeFilterPipelineAsync()
--- End of stack trace from previous location ---
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.<InvokeAsync>g__Logged|17_1(ResourceInvoker invoker)
at Microsoft.AspNetCore.Routing.EndpointMiddleware.<Invoke>g__AwaitRequestTask|6_0(Endpoint endpoint, Task requestTask, ILogger logger)
at Microsoft.AspNetCore.Authorization.Policy.AuthorizationMiddlewareResultHandler.HandleAsync(RequestDelegate next, HttpContext context, AuthorizationPolicy policy, PolicyAuthorizationResult authorizeResult)
at Microsoft.AspNetCore.Authorization.AuthorizationMiddleware.Invoke(HttpContext context)
at Universal.Server.Middleware.RoutingMiddleware.Invoke(HttpContext httpContext, IPolicyEvaluator policyEvaluator) in D:\a\universal\universal\src\Universal.Server\Middleware\RoutingMiddleware.cs:line 134
at Swashbuckle.AspNetCore.SwaggerUI.SwaggerUIMiddleware.Invoke(HttpContext httpContext)
at Swashbuckle.AspNetCore.Swagger.SwaggerMiddleware.Invoke(HttpContext httpContext, ISwaggerProvider swaggerProvider)
at Universal.Server.Middleware.SwaggerAuthenticationMiddleware.InvokeAsync(HttpContext context, RequestDelegate next) in D:\a\universal\universal\src\Universal.Server\Middleware\SwaggerAuthMiddleware.cs:line 42
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext()
--- End of stack trace from previous location ---
at StackExchange.Profiling.MiniProfilerMiddleware.Invoke(HttpContext context) in C:\projects\dotnet\src\MiniProfiler.AspNetCore\MiniProfilerMiddleware.cs:line 121
at AspNetCoreRateLimit.RateLimitMiddleware`1.Invoke(HttpContext context) in D:\a\universal\universal\src\AspNetCoreRateLimit\Middleware\RateLimitMiddleware.cs:line 109
at Microsoft.AspNetCore.Session.SessionMiddleware.Invoke(HttpContext context)
at Microsoft.AspNetCore.Session.SessionMiddleware.Invoke(HttpContext context)
at Microsoft.AspNetCore.Diagnostics.ExceptionHandlerMiddleware.<Invoke>g__Awaited|6_0(ExceptionHandlerMiddleware middleware, HttpContext context, Task task)
[17:34:46 WRN] No exception handler was found, rethrowing original exception.
[17:34:46 ERR] Connection ID "14987979561499681183", Request ID "8000e1a8-0000-d000-b63f-84710c7967bb": An unhandled exception was thrown by the application.
System.NullReferenceException: Object reference not set to an instance of an object.
@Adam - any ideas I’m stumped!