Version: 1.5.6
I actually can’t reproduce this and it seems to work as expected. Let me know if you can spot what I’m doing differently. Let me know if you need more information.
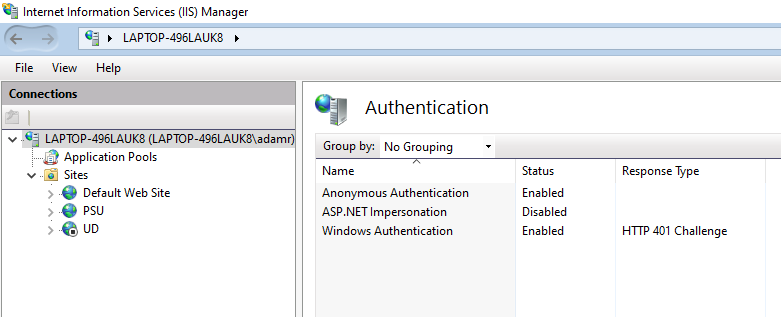
Server Auth Settings:
Web App Settings:
Web Config
<?xml version="1.0" encoding="utf-8"?>
<configuration>
<system.webServer>
<handlers>
<add name="aspNetCore" path="*" verb="*" modules="AspNetCoreModuleV2" resourceType="Unspecified" />
</handlers>
<aspNetCore processPath=".\Universal.Server.exe" arguments="" forwardWindowsAuthToken="true" stdoutLogEnabled="true" stdoutLogFile=".\logs\log" hostingModel="OutOfProcess" />
</system.webServer>
</configuration>
<!--ProjectGuid: 588ACF2E-9AE5-4DF1-BC42-BCE16A4C4EDE-->
AppSettings.json
{
"Kestrel": {
"Endpoints": {
"HTTP": {
"Url": "http://*:5000"
}
},
"RedirectToHttps": "false"
},
"ApplicationInsights": {
"InstrumentationKey": ""
},
"Logging": {
"Path": "%PROGRAMDATA%/PowerShellUniversal/log.txt",
"RetainedFileCountLimit": 31,
"LogLevel": {
"Default": "Debug",
"Microsoft": "Debug",
"Microsoft.Hosting.Lifetime": "Debug"
}
},
"AllowedHosts": "*",
"CorsHosts": "",
"Data": {
"RepositoryPath": "%ProgramData%\\UniversalAutomation\\Repository",
"ConnectionString": "%ProgramData%\\UniversalAutomation\\database.db",
"GitRemote": "",
"GitUserName": "",
"GitPassword": "",
"ConfigurationScript": ""
},
"Api": {
"Url": ""
},
"Authentication" : {
"Windows": {
"Enabled": "true"
},
"WSFed": {
"Enabled": "false",
"MetadataAddress": "",
"Wtrealm": "",
"CallbackPath": "/auth/signin-wsfed"
},
"OIDC": {
"Enabled": "false",
"CallbackPath": "/auth/signin-oidc",
"ClientID": "",
"ClientSecret": "",
"Resource": "",
"Authority": "",
"ResponseType": "",
"SaveTokens": "false"
},
"SessionTimeout": "25"
},
"Jwt": {
"SigningKey": "PleaseUseYourOwnSigningKeyHere",
"Issuer": "IronmanSoftware",
"Audience": "PowerShellUniversal"
},
"UniversalDashboard": {
"AssetsFolder": "%ProgramData%\\PowerShellUniversal\\Dashboard"
},
"ShowDevTools": false,
"HideAdminConsole": false
}
Endpoints
Testing (from PS7.1)
PS C:\Users\adamr> invoke-restmethod http://localhost:82/authed
Invoke-RestMethod: Response status code does not indicate success: 401 (Unauthorized).
PS C:\Users\adamr> invoke-restmethod http://localhost:82/test
PS C:\Users\adamr> invoke-restmethod http://localhost:82/authed -UseDefaultCredentials -AllowUnencryptedAuthentication
PS C:\Users\adamr> invoke-restmethod http://localhost:82/authed -Headers @{ Authorization = "Bearer eyJhbG///" }
I cannot access the Admin Console without authenticating.