BoSen29
December 13, 2019, 1:44pm
1
So i’ve tried to be fancy, and use the new oauth authentication with the fancy tokens.
However… cannot seem to find any reference to what return url is being passed:
I haven’t changed it from a functional “regular” Azure AD authentication, and currently is:https://dashboard.somedomain.com/signin-oidc
Any suggestions?
(pardon my Norwegian, “Sorry, we could not log you on” - loosely translated)
adam
December 13, 2019, 2:04pm
2
Ack. I need to get this in the documentation. Sorry about that: http://localhost:10001/signin-callback
adam
December 13, 2019, 2:04pm
3
I could also make this configurable.
BoSen29
December 13, 2019, 2:57pm
4
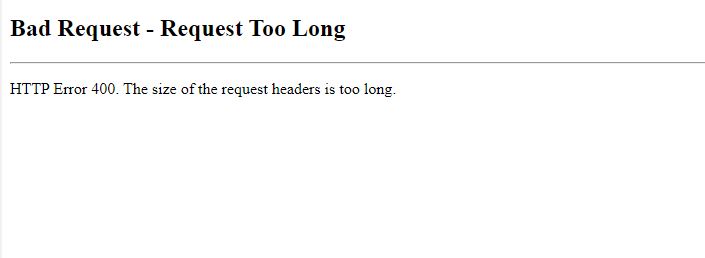
Works-ish.
Now i got a headersize related issue in IIS…
And after increasing:
Should i not include group memberships claims in the app-registration?
BoSen29
December 13, 2019, 2:59pm
5
clientside: 500 status error on fetch-service.jsx:56
adam
December 13, 2019, 3:12pm
6
I sure wish it would tell you what the unhandled exception was… Does it work if you don’t include the group claims?
BoSen29
December 13, 2019, 3:16pm
7
I’ll test it after dinner and update you
BoSen29
December 13, 2019, 4:14pm
8
Hi again @adam ,
Yep, no change with “null” for GroupMembershipclaims in the manifest.
The RESTAPI auth works like a charm, but that is a separate auth method.
Could i be misusing some variables anywhere which could lead to this, or is it IIS related issue?
BoSen29
December 13, 2019, 4:18pm
9
Yep, it’s my authorization policies…
However, i see no reason for these to fail.
All of them are hardcoded to $User.Identities.Name checks, as i am lazy and haven’t gotten around to utilizing groups.
Any ideas?
adam
December 13, 2019, 4:38pm
10
Do you have debug logging on or just warning level? I wonder if there is more info in the log. Otherwise, I can look at adding some additional logging to see if we can catch that unhandled exception and get it in a kit for you to play with.
BoSen29
December 13, 2019, 4:48pm
11
I’ll mail you the relevant logs dude
Just checking if it’s 1 of 4 auth policies, or multiple.
BoSen29
December 13, 2019, 4:59pm
12
UD took a DECENT performance hit aswell with the openid authentication.
42 Endoints idle, checked the diagnostics page. Regular numbers.
(Settings the auth policy to “return $true” works)
adam
December 13, 2019, 5:01pm
13
I think it’s actually a problem with this: https://github.com/ironmansoftware/universal-dashboard/issues/1372
I think I’ll roll out a 2.8.1 build next week because of that issue. Can you give the nightly enterprise build a shot and see if it’s the same issue with performance?
BoSen29
December 13, 2019, 5:03pm
14
Hi,
Is it out already?
adam
December 13, 2019, 5:04pm
15
Well, let me make sure. Doesn’t look like there was a nightly from last night.
1 Like
BoSen29
December 13, 2019, 5:06pm
16
Your theory makes sense to my logfile of authpolicies.
Basically i did add-content $User | convertto-json “logfile”
76KB of log file on first login.
I’m hopeful :-3
adam
December 13, 2019, 5:08pm
17
Yurp…
And Houston down! The build failed last night so I’ll fix that up and get something for you tomorrow that should prevent this from happening.
BoSen29
December 13, 2019, 5:12pm
18
It’s friday afternoon dude, are you ever “off work”?
Don’t stress it dude, i can just revert to the old auth method and do some component work if i get bored
1 Like
BoSen29
December 13, 2019, 5:20pm
19
Found the main reason for the performance issue by the way:
Could probably have truncated the logfile, but 20MB isn’t that big for a logfile…
1 Like
BoSen29
December 16, 2019, 7:30am
20
Hi again,
Is this the relevant nightly build?
Lack of changelogs on the enterprise edition